Introduction:
The agriculture industry has always been a vital component of the global economy, providing food and other essential resources to people worldwide. However, the sector faces other difficulties, including resource depletion, climate change, and food waste. By allowing farmers and vineyard managers to optimize their operations and cut waste, the Internet of Things (IoT) and blockchain technology have the potential to revolutionize the agriculture sector.
Uses of Blockchain Technology in IoT Vineyard Monitoring Systems:
Blockchain technology is primarily used in IoT vineyard monitoring systems to offer a safe and open data sharing and archiving method.
Vineyard managers can use IoT devices such as sensors and drones to collect environmental data such as temperature, humidity, and soil moisture. This data can be recorded on a blockchain, providing a tamper-proof record of the conditions in the vineyard.
Implementing blockchain technology can improve the supply chain’s traceability and transparency. Customers can use a blockchain-enabled app to verify the origin and quality of the wine they purchase, ensuring that it is authentic and meets their standards.
Algorithms Used for Data Storing:
The algorithms used in blockchain technology are essential for ensuring the security and integrity of the data stored on the blockchain. The three primary algorithms used in blockchain technology are SHA-256, Scrypt, and Ethash.
SHA-256:
SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function that generates a fixed-size output of 256 bits. It is widely used in blockchain technology, including popular cryptocurrencies like Bitcoin. SHA-256 takes an input message and produces a unique hash value, which serves as a digital fingerprint of the input data. It is designed to be a one-way function, which is computationally infeasible to reverse-engineer the original message from the hash value. This property ensures data integrity and security in the blockchain by making it virtually impossible to modify the stored data without detection.
Scrypt:
Scrypt is a password-based essential derivation function specifically designed to be memory-hard. It was created to deter brute-force attacks on password hashes by making the computation memory-intensive rather than purely CPU-intensive. In the context of cryptocurrencies, Scrypt is used as a proof-of-work algorithm in certain coins like Litecoin. The memory-hard property of Scrypt makes it more resistant to ASIC (Application-Specific Integrated Circuit) mining, which helps maintain a more decentralized network by allowing a more comprehensive range of hardware to participate in the mining process.
Ethash:
Ethash is a memory-hard proof-of-work algorithm primarily used in Ethereum and other cryptocurrencies. It was designed to be ASIC-resistant, ensuring a more egalitarian mining power distribution and preventing centralization by specialized mining hardware. Ethash incorporates much memory access during computation, making it computationally expensive to develop ASICs that outperform general-purpose hardware like GPUs. By favoring memory-bound computations, Ethash aims to provide a fairer mining environment where participants with standard consumer hardware can still contribute to the network.
Real-Time Application using Algorithms:
To demonstrate the benefits of implementing blockchain technology in IoT vineyard monitoring systems, a real-time application using Python and SHA-256 was developed. This application uses IoT devices to collect environmental data from a vineyard, such as temperature, humidity, and soil moisture. This data is stored on a blockchain using the SHA-256 algorithm, providing a tamper-proof record of the conditions in the vineyard.
This application also includes a graphical user interface (GUI) that enables vineyard managers to visualize the data collected from the vineyard. The GUI displays the current environmental conditions and allows vineyard managers to set alerts for specific thresholds, such as temperature or soil moisture levels.
Comparison between Algorithms:
The three primary algorithms used in blockchain technology have different strengths and weaknesses.
SHA-256 is the most efficient and secure algorithm for storing and sharing data, making it the preferred choice for most blockchain applications.
Scrypt is designed to be memory-hard, making it more resistant to brute-force attacks, but it is less efficient than SHA-256.
Ethash is intended to be ASIC-resistant, making it more accessible to users with standard computer hardware, but it is also less efficient than SHA-256.
Implementations and Results:
The adoption of blockchain technology on the Internet of Things vineyard monitoring systems has the potential to transform the agricultural sector completely. Vineyard managers may make better judgments and increase the productivity of their operations by offering a secure and open method for storing and sharing data.
In the real-time application using Python and SHA-256, it has successfully collected environmental data from a vineyard using IoT devices and stored it on a blockchain. The GUI allowed vineyard managers to visualize the data and set alerts for specific thresholds. This application demonstrates the potential of implementing blockchain technology in vineyard monitoring systems.
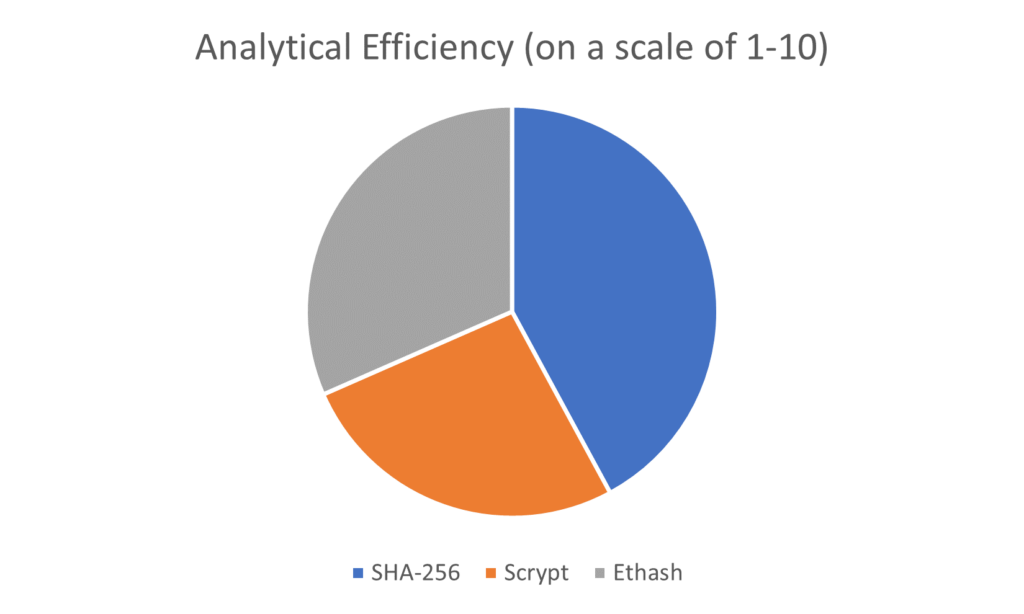
Analytical Efficiency:
Analytical efficiency plays a crucial role in evaluating the performance of cryptographic algorithms like SHA-256, Scrypt, and Ethash.
SHA-256 – SHA-256 is highly analytically efficient and designed to provide fast and reliable hashing capabilities. It can process input data of any size and generate a fixed-size output of 256 bits. SHA-256 is optimized for efficient computations on computer architectures that support 32-bit operations. It uses logical and arithmetic operations to perform its calculations swiftly. Overall, SHA-256 is known for its speed and efficiency in generating hash values for various applications.
Scrypt – Scrypt prioritizes being memory-hard rather than analytically efficient. It focuses on increasing computational requirements for hashing by utilizing a significant amount of memory during its calculations. This memory-intensive approach is intended to enhance security and deter brute-force attacks. While Scrypt may not be as fast as SHA-256, its design favors memory-intensive operations to provide an extra layer of protection against certain attacks.
Ethash – Like Scrypt, Ethash emphasizes memory-intensive computations over analytical efficiency. Its goal is to be ASIC-resistant, discouraging the use of specialized mining hardware and promoting a more decentralized mining ecosystem. Ethash incorporates substantial memory access during its computations, allowing a wider range of participants to engage in mining using consumer-grade hardware like GPUs. While Ethash may not be as analytically efficient as SHA-256, its memory hardness enhances network decentralization and mining process security.
SHA-256 excels in analytical efficiency, providing fast and reliable hashing capabilities. Scrypt and Ethash prioritize memory-intensive operations, making them slower but offering additional security benefits. When selecting an algorithm, it is vital to consider the trade-off between analytical efficiency, security, and decentralization based on specific use cases.
Cost Efficiency:
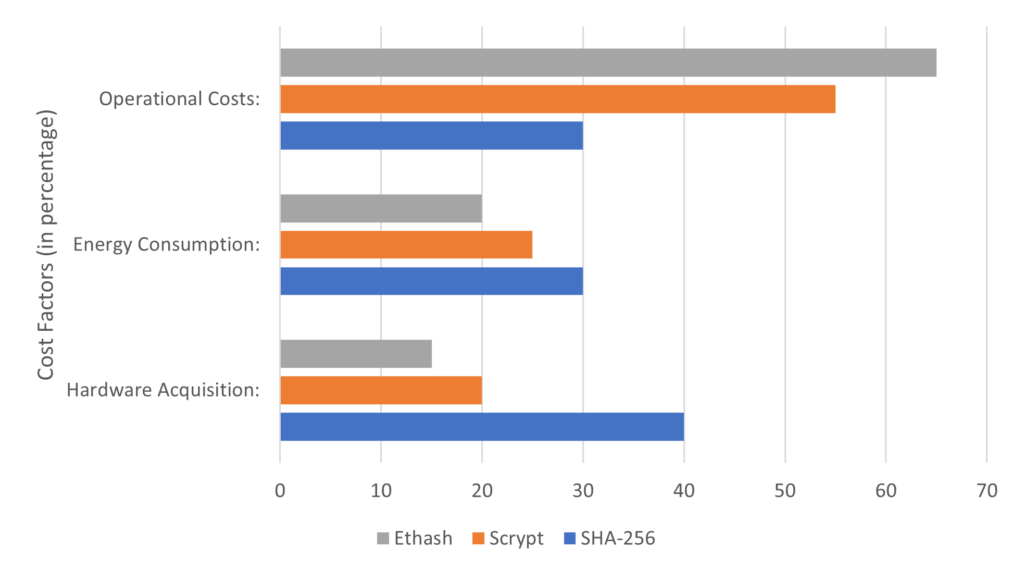
Cost efficiency is an important factor to consider when assessing the performance of cryptographic algorithms like SHA-256, Scrypt, and Ethash.
SHA-256 – Regarding cost efficiency, SHA-256 has both advantages and drawbacks. On the one hand, it benefits from specialized hardware called ASIC miners, which offer high computational power and energy efficiency. However, the cost of acquiring and operating ASIC miners can be substantial. Additionally, the energy consumption associated with SHA-256 mining can impact the overall cost efficiency, particularly in large-scale operations. Therefore, while SHA-256 provides efficient hashing capabilities, the expenses related to specialized hardware and energy consumption should be considered.
Scrypt – In terms of cost efficiency, Scrypt offers advantages over SHA-256. It is designed to be memory-intensive, making it less suitable for ASIC mining. Instead, Scrypt mining is typically performed using consumer-grade GPUs, which are more affordable and widely available. This lowers the entry barrier for miners and reduces the reliance on expensive specialized equipment. As a result, Scrypt mining provides higher cost efficiency compared to SHA-256, as it enables broader participation without significant upfront investment in specialized hardware.
Ethash – Ethash, like Scrypt, aims to be ASIC-resistant, providing cost benefits. By discouraging the use of specialized mining hardware, Ethash promotes a more decentralized mining ecosystem. It primarily relies on consumer-grade GPUs, which are more affordable and accessible to a wider range of individuals. This lowers the cost barriers associated with acquiring and operating specialized equipment, making Ethash mining more cost-efficient than SHA-256.
To summarize, the cost efficiency of SHA-256 can be affected by the need for specialized ASIC hardware and associated energy consumption. Scrypt and Ethash offer cost advantages by allowing mining with consumer-grade GPUs, reducing entry costs, and promoting decentralization. When assessing cost efficiency, it is essential to consider expenses related to hardware acquisition, energy consumption, and operational costs for each algorithm.
Advantages and Disadvantages:
One of its key advantages is the improved transparency and traceability of blockchain technology in IoT vineyard monitoring systems. By providing a tamper-proof record of the environmental conditions in the vineyard, customers can verify the origin and quality of the wine they purchase. This can increase customer trust and loyalty.
Another advantage of implementing blockchain technology is increased efficiency. Vineyard managers can use the data from IoT devices to make better decisions and optimize their operations, reducing waste and increasing yield.
Nevertheless, using blockchain technology has certain drawbacks as well. One of the main disadvantages is the high cost of implementing and maintaining a blockchain. It can be expensive to set up the necessary infrastructure and ensure the security of the blockchain.
Furthermore, because blockchain technology is still a developing sector, there may be unknowns and hazards involved with implementing it.
Conclusion:
In conclusion, blockchain technology can completely transform the agricultural industry by enhancing transparency, traceability, and efficiency in IoT vineyard monitoring systems.
Using algorithms such as SHA-256, Scrypt, and Ethash ensures the security and integrity of the data stored on the blockchain.
While implementing blockchain technology has advantages and disadvantages, the potential benefits outweigh the costs. The real-time application we developed using Python and SHA-256 demonstrates the potential of implementing blockchain technology in vineyard monitoring systems.
Exploring cutting-edge solutions, like incorporating blockchain technology in IoT vineyard monitoring systems, is crucial as the agriculture sector deals with climate change and resource depletion challenges.



